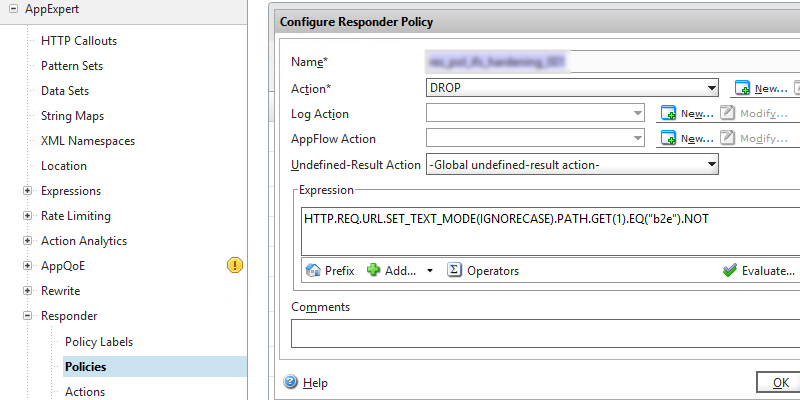
Sometimes I wonder; what was that command again to get the a particular output.
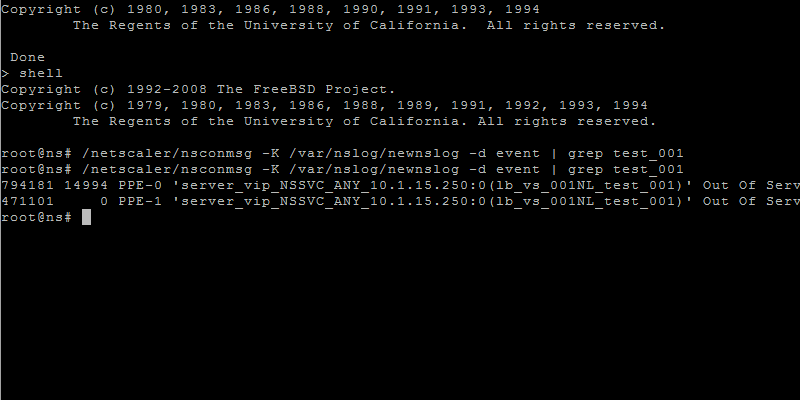
You can for example run the following command for the newnslog files to get information about the "states" of all your created objects like vservers or services.
/netscaler/nsconmsg -K /var/nslog/newnslog -d event
If a vserver goes down or up you will see it with this command.
Every 2 days, the NetScaler makes a new log file. Go to /var/nslog/ and do a ls -l to show the timestamp information.
Also you can can use the PIPE and GREP commands to get specific information that you want to see. It also works with files that are compressed like tar.gz.
For example:
/netscaler/nsconmsg -K /var/nslog/newnslog.63.tar.gz -d event | grep exchange
Use the nsconmsg command to only display a span of time within the given file, as shown in the following example:
/netscaler/nsconmsg -K /var/nslog/newnslog -s time=22Mar2007:20:00 -T 7 -s ConLb=2 -d oldconmsg
Where
s time=22Mar2007:20:00 is start at March 22, 2007 at exactly 8 p.m.
T 7 is display seven seconds of data
s ConLb=2 is a detail level for load balancing statistics
d oldconmsg is display statistical information
Here is also a short Citrix article how to get some statistics from the newnslog.
Uncompress an archived log file:
gunzip newnslog.21.gz
Discover the time period covered by the log:
nsconmsg -K newnslog.21 -d setime
View load-balancing statistics from the archived log:
nsconmsg -K newnslog.21 -s ConLb=2 -d oldconmsg
Extract logging information for a shorter duration:
nsconmsg -K newnslog.21 -s time=12Jan2006:00:00 -k short_log.nsl -T 1200 -d copy
Start the log process for newnslog:
nsconmsg -k /var/nslog/newnslog -T 172800 &
View the time span of the current newnslog file:
nsconmsg -K newnslog -d setime
View the time span of the archived newnslog file:
zcat filename | nsconmsg -K pipe -d setime
View events in the current newnslog file:
nsconmsg -K newnslog -d event
View console messages in the current newnslog file:
nsconmsg -K newnslog -d consmsg
View counter values in the current newnslog file:
nsconmsg -K newnslog -d stats
View counter values in the current newnslog file:
nsconmsg -K newnslog -d stats -d current
View non-zero counter values in the current newnslog file:
nsconmsg -K newnslog -d statswt0 -d current
to display event information, such as entity up/down, alerts and configuration saves in the shell:
nsconmsg -K newnslog -d event
Display CPU usage in the shell:
nsconmsg -K newnslog -s totalcount=200 -g cpu_use -d current
Display memory utilization in the shell:
nsconmsg -s ConMEM=1 -d oldconmsg
Display established HTTP connections in the shell:
nsconmsg -j server_NSSVC_HTTP_vserver -d current
Display load balancing statistics in the shell:
nsconmsg -K newnslog -s ConLb=x -d oldconmsg
This command gives basic information when x=1 and detailed information when x=2.
use the following command to view traffic distribution from the shell.
nsconmsg -K /var/nslog/newnslog -s time -s ConLB=2 -2 distrconmsg
to display load-balancing information in the shell.
nsconmsg -s ConLb=1 -d oldconmsg
Display monitoring statistics in the shell.
nsconmsg -K newnslog -s ConMon=x -d oldconmsg
This command gives basic information when x=1 and gives detailed information when x=2.
View SSL stats for front-end connections:
nsconmsg -K newnslog -s ConSSL=1 -d oldconmsg
View SSL stats for back-end connections:
nsconmsg -K newnslog -s ConSSL=2 -d oldconmsg
View SSL stats for front and back-end connections:
nsconmsg -K newnslog -s ConSSL=3 -d oldconmsg
Display content switching statistics in the shell.
nsconmsg -K newnslog -s ConCSW=1 -d oldconmsg
Display compression statistics in the shell.
nsconmsg -K newnslog -s ConCMP=x -d oldconmsg
This command gives old compression method related statistics when x=1 and gives new compression method related statistics when x=2
Display integrated caching statistics in the shell.
nsconmsg -K newnslog -s ConIC=1 -d oldconmsg